Office 365 Administrator Account Best Practices
One of the best things about Office 365 is that it can be accessed and administered from any internet-connected device. Unfortunately, this also means that you can potentially be hacked from any internet-connected device.
Here we are going to outline a few basic Best Practices around Microsoft Office 365 Administrator accounts to reduce the chances that you will become victim to one of these attacks.
We will be covering the following topics:
- Use Long Complex Passwords
- Use a separate Administrator Account
- Enable Multi-Factor Authentication
- Use a separate Administrator Account for PowerShell Access
Use Long Complex Passwords
This one should be obvious, but it’s very important so we’re going to reiterate it again.
You should use a password that is 10 characters long and made up of a mixture of capital and lower case letters, numbers and special characters.
Never use the same password on more than one site.
We know this can be a bit of a pain, but it is definitely the best thing you can do to prevent identity theft. We recommend using a Password Manager to keep track of them all.
Use a Separate Administrator Account
Office 365 Administrator permissions should never be applied to a users general day to day account.
For example:
Imagine you have an Office 365 account called alan@contoso.com that you use everywhere to get your email, access SharePoint and use to authenticate to other Office 365 services. This account should be a standard user account with no Administrator permissions.
You should create a separate account called alan_admin@contoso.com that has Administrator access and use this account only for logging in to the Microsoft Portal or PowerShell.
This user account doesn’t even require an Office 365 licence as it most likely doesn’t need a mailbox. This means you will not be charged by Microsoft for this additional Administrative account.
It is recommended that you create this account on the built-in .onmicrosoft.com domain, rather than one of your custom domains. This is especially useful if you currently use, or intend to use, DirSync. This allows you to log in as a non-federated account in the event that something happens with your on-premises Admin accounts.
The create an Administrator account section below shows you how to create a new administrator user.
Enable Multi-Factor Authentication
Microsoft now offer Multi-Factor Authentication for Administrator accounts in Office 365. This adds an extra layer of security to your administrator account preventing hackers from guessing your password.
Note: Once you enable Multi-Factor authentication on an Administrator account it can no longer be used to log into Office 365 using Microsoft PowerShell. For this reason we strongly recommend you follow all the steps in this article to create separate Administrator accounts for PowerShell and Administration. If you try and use Windows PowerShell with this account you will get an error that says “Admin is not allowed to create session using app password”.
Enabling Two Factor Authentication is fairly straight forward.
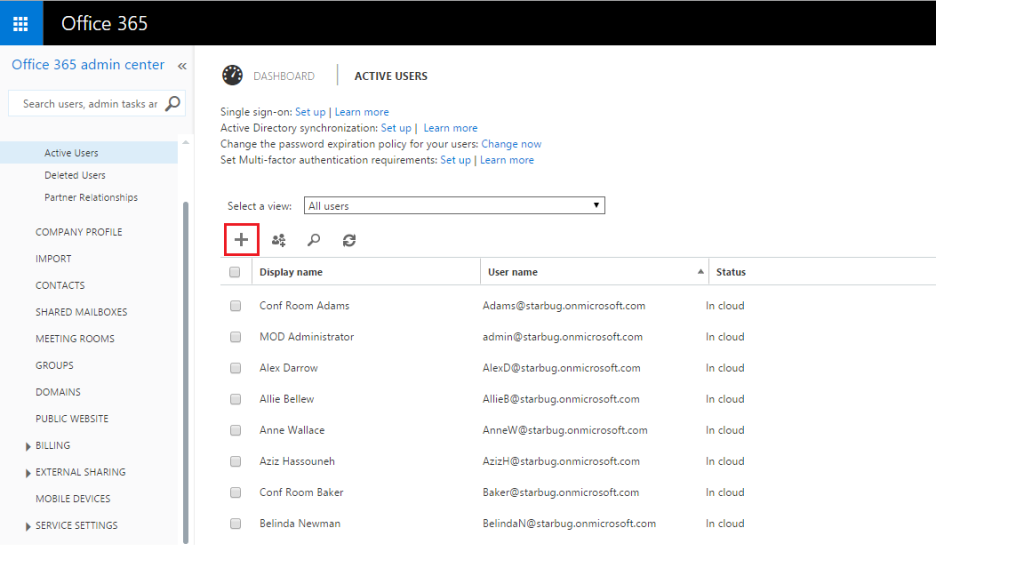
First, log into the Office 365 Admin Portal and navigate to the user management section.
Click Set Up next to Multi-Factor Authentication at the top.

Tick the box next to the user you are enabling Multi-Factor Authentication for and click Enable in the Quick Steps section and you will be asked to verify your choice.

Now that you have enabled Multi-Factor authentication you need to log out of Office 365 and log back in as the user you selected above.
On first login you will be prompted to configure the Multi-Factor authentication settings.
Choose the two factor Authentication method. We recommend text message as it is available in most countries and very simple to use.
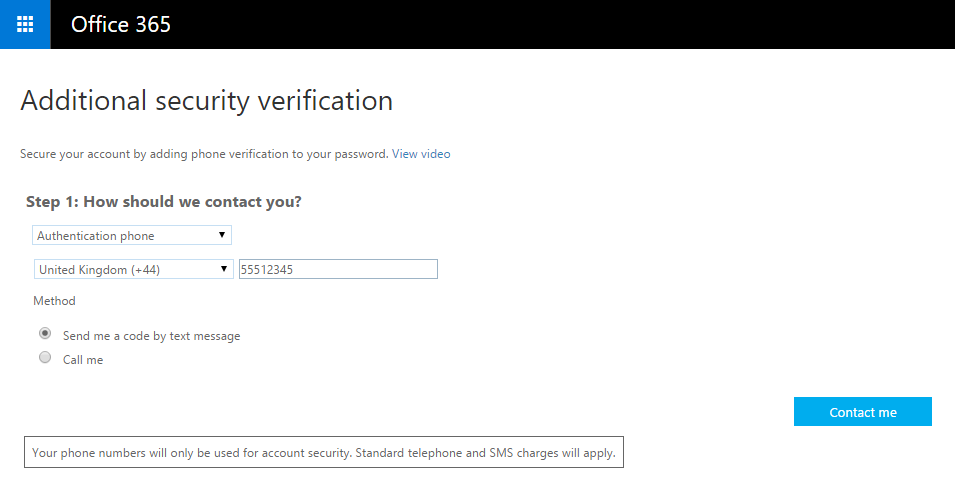
Microsoft will send you a text message with a 6 digit code each time you try and log in. You then enter this code along with your password to confirm it’s actually you logging in.
Microsoft will now send you a test code to verify that it is all set up correctly.
From now on when you log into the Office 365 or Windows Azure AD Administration Portal you will be prompted to enter the code texted to your phone.
Use a separate Administrator Account for PowerShell Access
Now that you’ve enabled Multi-Factor Auth on your Administrator account it will be impossible to connect to Office 365 using PowerShell.
If you try, you’ll see an error like this:
PS C:\Users\burns_000\Desktop> .\connect-ps.ps1
cmdlet Get-Credential at command pipeline position 1
Supply values for the following parameters:
Credential
New-PSSession : [ps.outlook.com] Connecting to remote server ps.outlook.com failed with the following error message : Access is denied. For more information, see the about_Remote_Troubleshooting Help topic. At C:\Users\burns_000\Desktop\connect-ps.ps1:3 char:12 + $session = New-PSSession -ConfigurationName Microsoft.Exchange -ConnectionUri “h … + ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : OpenError: (System.Manageme….RemoteRunspace:RemoteRunspace) [New-PSSession], PSRemotin gTransportException + FullyQualifiedErrorId : AccessDenied,PSSessionOpenFailed Import-PSSession : Cannot validate argument on parameter ‘Session’. The argument is null. Supply a non-null argument and try the command again. At C:\Users\burns_000\Desktop\connect-ps.ps1:4 char:18 + Import-PSSession $session + ~~~~~~~~ + CategoryInfo : InvalidData: (:) [Import-PSSession], ParameterBindingValidationException + FullyQualifiedErrorId : ParameterArgumentValidationError,Microsoft.PowerShell.Commands.ImportPSSessionCommand
What we need to do instead is create another Administrator account, which doesn’t have Multi-Factor Authentication enabled and use it only for accessing PowerShell.
This administrator account will be disabled unless we explicitly want to use it. For most people this will not be an issue as they only connect to Office 365 using PowerShell once every few weeks.
To create another Administrator account we must again log into the Office 365 Admin Portal and navigate to the user management section.
Click the Plus button at the top to add a new user.

Now you need to log out of the Office 365 Admin portal and log back in as the newly created PowerShell user.
You can now use this user to log in to Office 365 using PowerShell.
Here’s the important bit: When you’re not using this account to log in to PowerShell, you should Set Sign In Status to Blocked.
To do this, log into the Office 365 Admin Portal, navigate to the users section and double click your PowerShell User to modify the account settings.

Now set the Sign-In Status to Blocked.
This will mean that no-one can use the account to administer Office 365 until you re-enable this option. You should only enable it when you are actually performing administration tasks.
Take the next step towards advanced SaaS management with our Office 365 reporting software